As an aws customer you benefit from a data center and network architecture that is built to meet the requirements of the most security sensitive organizations.
Aws ec2 container service security.
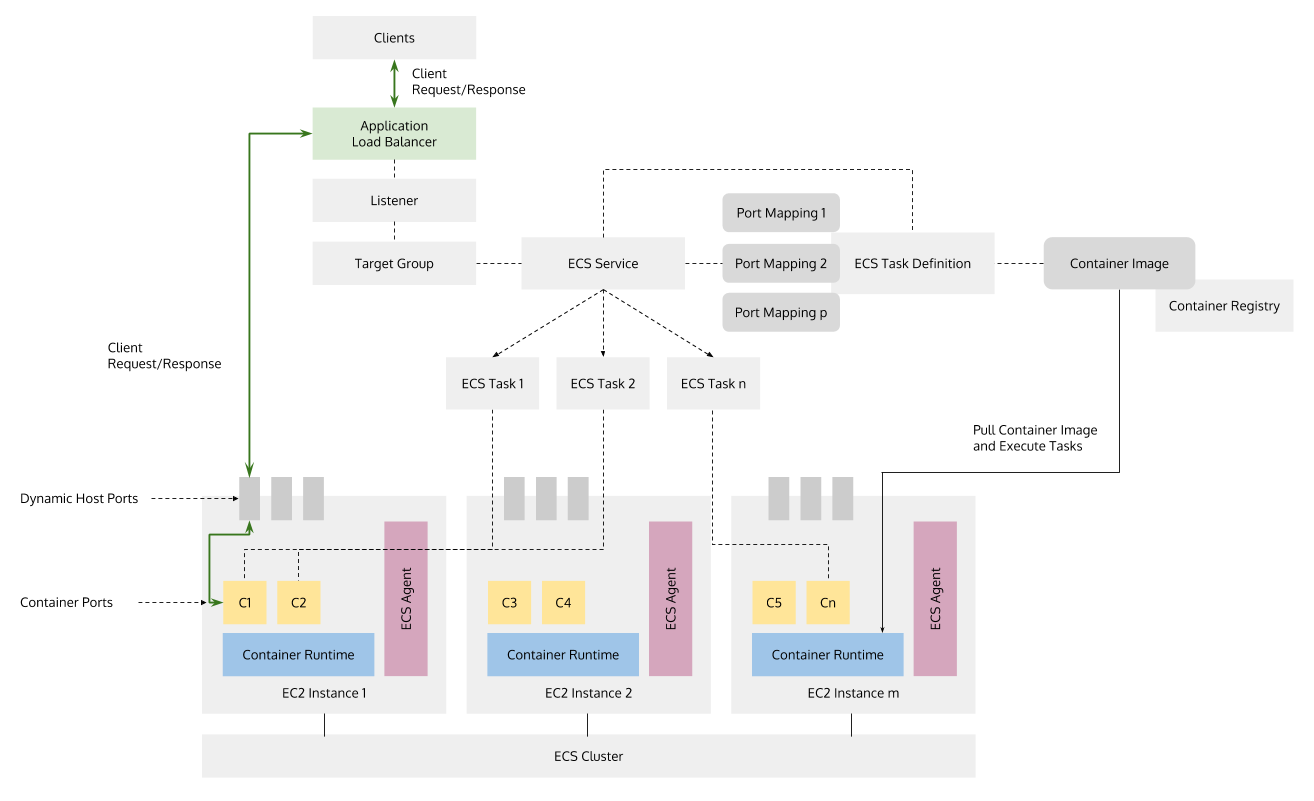
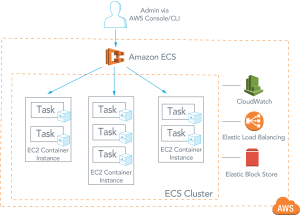
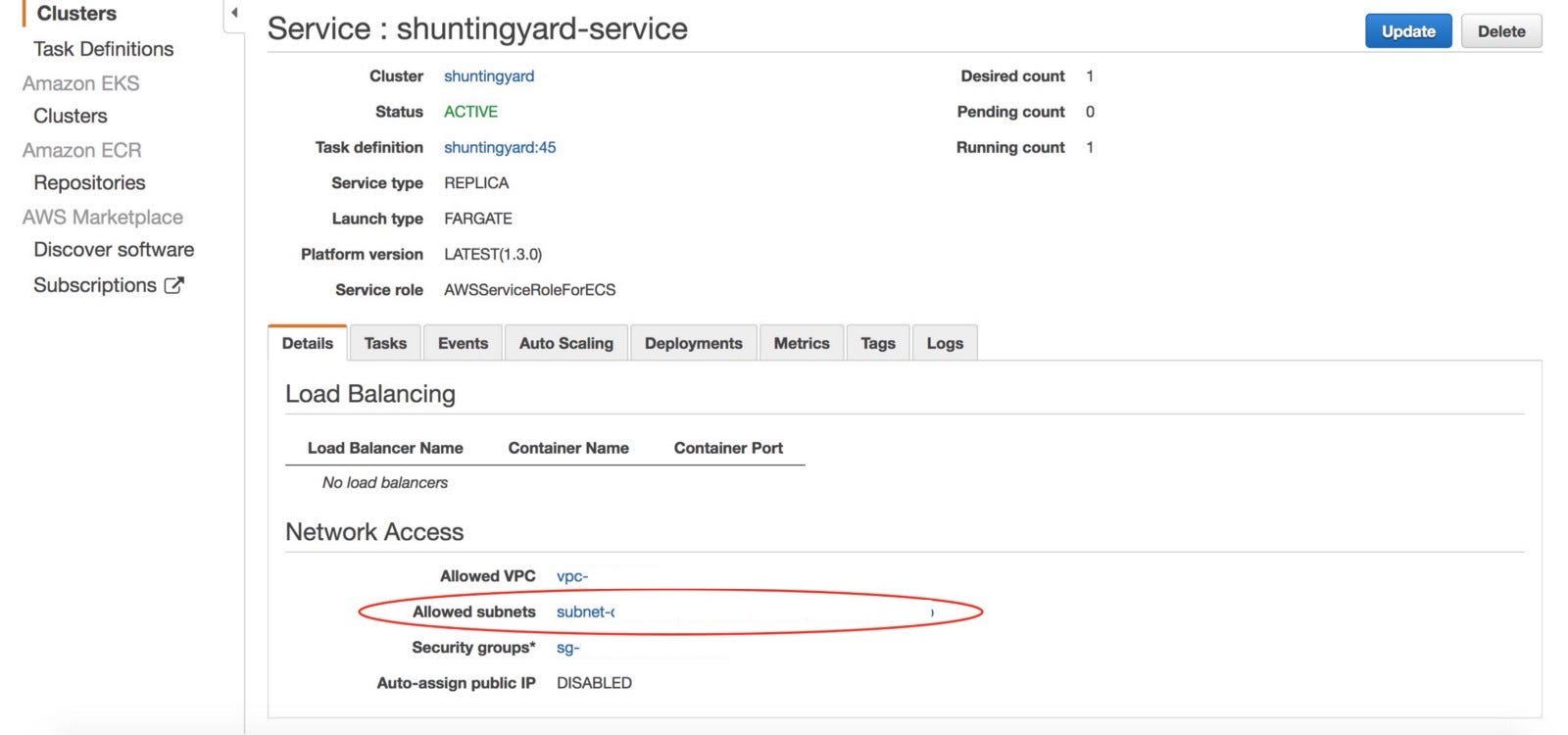
The tasks can take advantage of iam roles security groups and other aws security features.
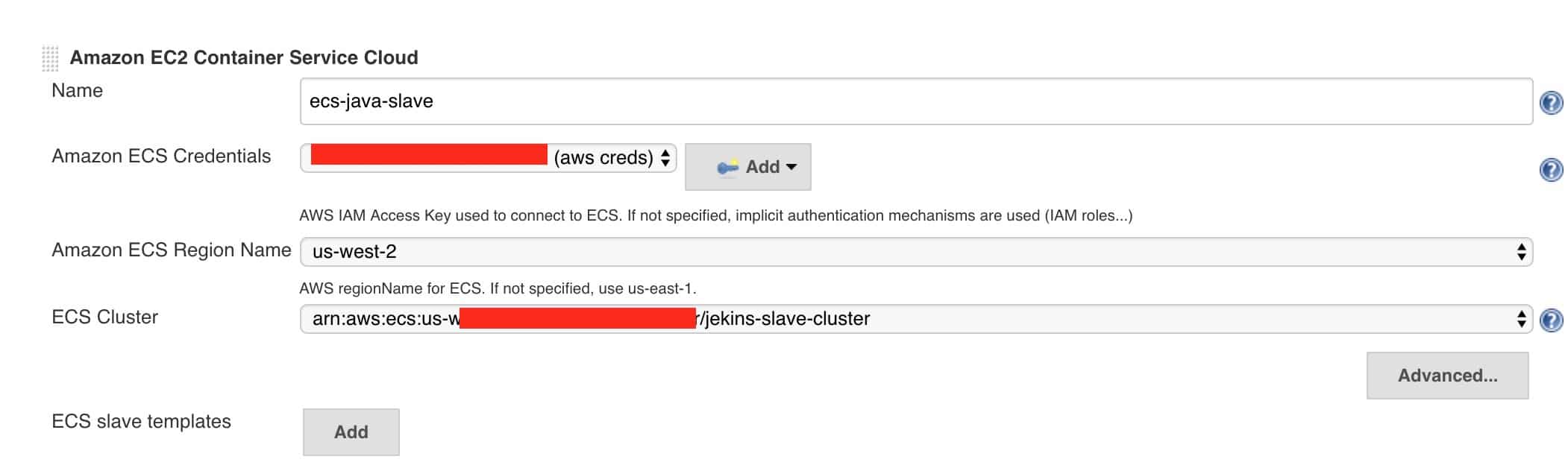
Using ec2 container service ecs was designed to be easy to set up and.
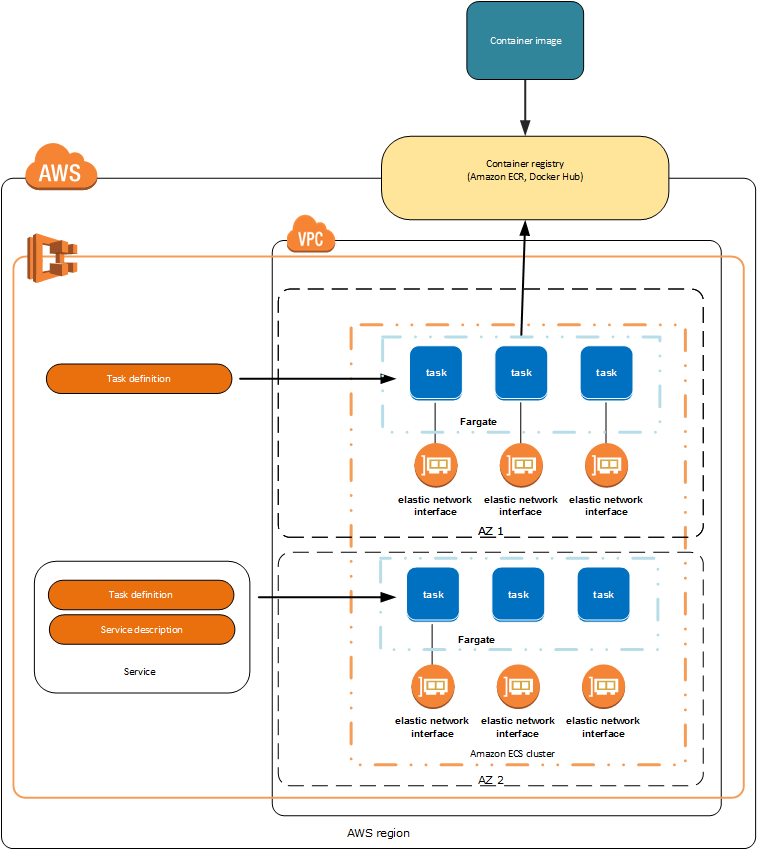
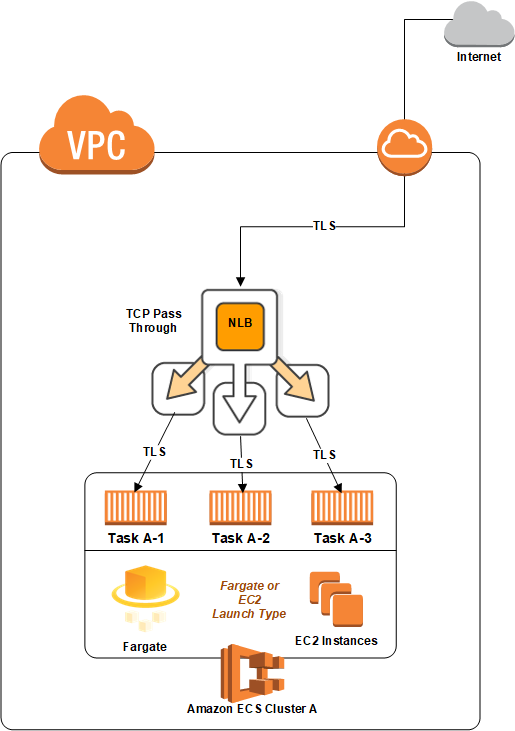
Amazon elastic container service amazon ecs is a fully managed container orchestration service.
Since your applications will run on ec2 instances you will have access to all the security controls generally available to those resources.
There are however security concerns with docker.
Customers such as duolingo samsung ge and cookpad use ecs to run their most sensitive and mission critical applications because of its security reliability and scalability.
Aws also provides you with services that you can use securely.
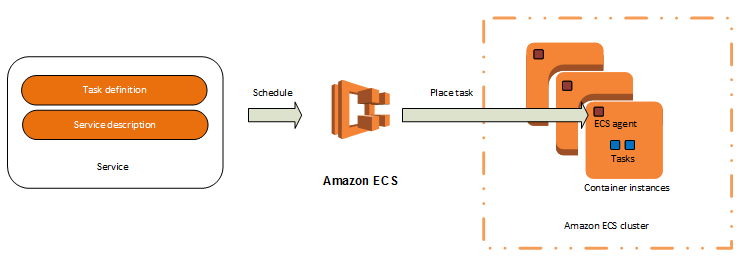
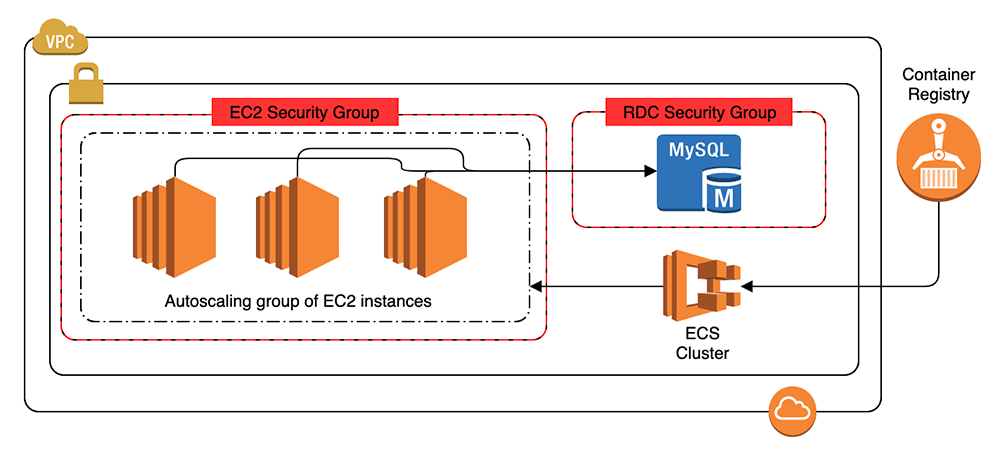
The containers are launched on ec2 instances that you own and control.
Security in amazon elastic container service cloud security at aws is the highest priority.
Create an iam user.
Note your aws account number because you ll need it for the next task.
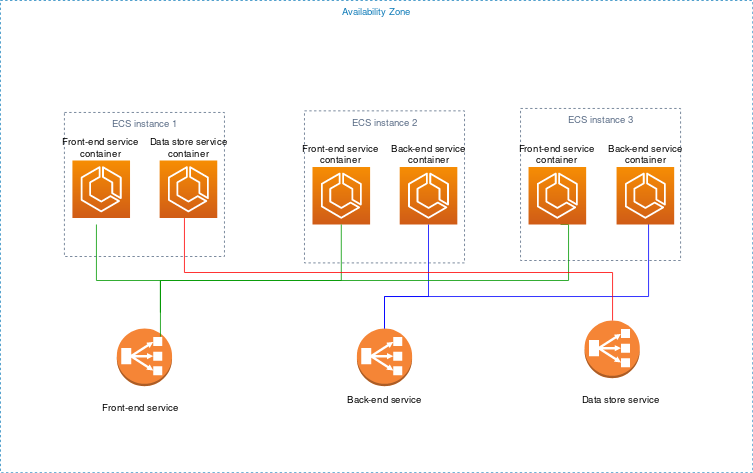
Containers run in a multi tenant environment and can communicate with each other only across defined interfaces.
Third party auditors regularly test and verify the effectiveness of our security as part of the aws compliance programs.